Definition:
The monitoring of entire networks from the perspective of information security. That is, the emphasis is placed on:- Identifying potential attacks and suspicious actions
- Identifying manifestations of security weaknesses
- Identifying the sources of all of these, and treating them accordingly.
SIEM
An automated system that monitors and collects security alerts and events relevant to security, from the entire network. According to predetermined settings, the information is collected, concentrated and sent to the SOC engineer. The logs are saved in the system's database, and the system alerts in real time on occurrences that require immediate attention. It actually does half the of the work for the SOC engineer, as all relevant material is collected and served to the engineer. The role of the SOC engineer is to know how to analyze the information properly, and react accordingly. And in short, a system that looks for and collects "fishy" events on a particular network. An example of a suspicious event: usage of the "Mimi Katz" program on the internal network is very fishy. The work in a SOC (Security Operations Center) mainly consists of scanning logs and reading alerts. The enginneer needs to know how to search for logged events (as well as how to search for other related information) , and know what he/she needs to search for.The record structure.
The log entries are arranged according to timestamps and each entry has a date and an exact timestamp of when it had occured. In addition, the record will include the IP addresses involved in the event, the remote address and the address of the device within the network, the ports involved (local and remote), and whether the connection between the IP addresses is incoming or outgoing (that is, whether the local device is receiving or sending packets). Suspicious activities on the local network:- Creating new user accounts, or editing existing ones.
- Messing with registry entries.
- Connections to suspicious external parties, or ip addresses that there is no clear justification for communicating with (for example, an IP that is not known to belong to a customer, or communication with an IP address from a foreign country for no apparent reason).
- Attempts to turn off/mess with the firewall and/or antivirus. (eg. trying to turn them off via Powershell).
Ways of dealing with and managing events in real time:
The most effective way - disconnecting the network cable/turning off the router physically, or turning off the network adapter through the computer's settings. No communication => no threat. But this is considered OVERKILL and a particularly extreme action that will only be carried out in extreme cases when there is no other choice. Companies need their servers, and any time their servers are offline they lose money. Another method - closing all of the ports (both necessary and unnecessary) on the firewall. As well as closing all unnecessary and necessary network available services. Yet another, more granular solution is closing all of the suspicious ports/services specifically on the firewall but leaving the rest of them open and available.. By suspicious I mean potentially utilized as an attack vector.Important signs and commands in the SOC field.
In the SOC field it is important to know how to look for signs of suspicious events, as a backup or as an additional measure to the SIEM system. The engineer can thus confirm the suspicions that had arisen as a result of the SIEM monitoring, or alternatively, check manually as an alternative to an improperly configured/temporarily non-functioning SIEM. The engineer can connect to the relevant computer/network component via SSH and look for signs of a security problem.- Checking the startup folder which contains files and programs that are configured to automatically run when the computer starts. (A hacker can plant files there in order to gain permanent access to the system.) In order to get to the startup folder, press the winkey+r key -> in the new window that will open (the Windows run window), type "msconfig" without quotes, and press enter. -> The msconfig settings window will open-> click on the "boot"\startup tab.-> Located here are all of the files that are configured to run when the computer is restarted. Check that all of the files are legitimate, and if not deactivate them. (By marking the file and selecting the "Disable" option).
- Checking in the task scheduler regarding triggers entered to activate suspicious files. Again, here too, a hacker can insert triggers in order to achieve automatic activation of files/viruses and thus achieve persistence on the system. In order to get to the event scheduler, press winkey+r-> in the window that opens, type taskschd.msc and press enter -> here all the triggers appear (events defined as those in response to which a file will be activated), and the files they are configured to activate. -> Search for files that should not run on the computer, and set the activated event as "inactive".
- Searching for registry values in folders that are designed to hold keys of values that are activated at the computer's startup. These values are links to different files, and if the hacker creates a key with a value that links to the virus he had planted, he will be able to gain access to the system. In order to check the values in the registry: press the winkey+r-> in the dialog box that opens, type regedit -> the registry will open -> check all of the links to files found in the key values in the relevant hives.
- HKLM/SOFTWARE/MICROSOFT/WINDOWS/CURRENT_VERSION/RUN
- HKLM/SOFTWARE/MICROSOFT/WINDOWS/CURRENT_VERSION/RUN_ONCE
- HK_LOCAL_USER/SOFTWARE/MICROSOFT/WINDOWS/CURRENTVERSION/RUN
- HK_LOCAL_USER/SOFTWARE/MICROSOFT/WINDOWS/CURRENTVERSION/RUN_ONCE
Important commands - for verifying threats or strengthening suspicions.
Netstat -nbt | find “ESTABLISHED” - Displays a detailed list of all active network connections including their respective ports On the left will be the local IP (that is, the local device's IP address, and the local port, and to the right will be the remote IP address and the remote port. The "-nbt" flag shows the user which software/service the connection is using, and filters the output to only actively ongoing connections. The command without the pipe character ("|") and the second half of the command (that is just typing "netstat -nbt" without the pipe) produces more output which is non-specific to active connections (it's actually the same command without filtering for active connections only). If there is an unexplained connection, you can take the remote IP address and perform the 'nslookup' command on it at the command prompt: nslookupAppendix - how to add firewall rules and close ports.
Every computer has a different firewall, Linux operating systems utilize iptables, in Windows the default is the Windows firewall (comes with the defender). To get to the firewall settings: Enter the control panel. You can press winkey+r and type in "control panel". In the control panel, enter security settings. From here you have to enter the firewall settings.A.
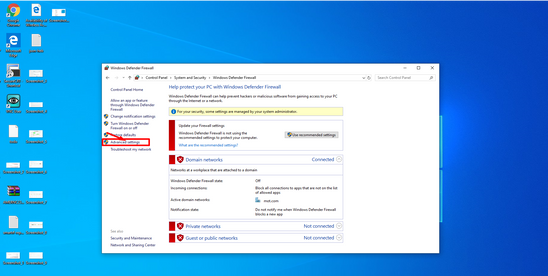
B.
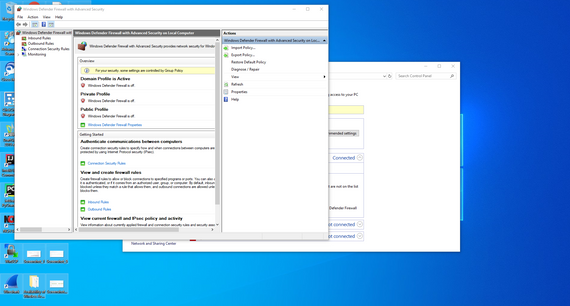
This is the new window that will open. Here you can add new rules to the firewall. Setting up firewall rules is pretty intuitive. You can define rules that allow access, and those that prohibit access. The rules can apply to a single port or a range of ports. Likewise, a rule can apply to any and all IP addresses, be specific to a specified IP address, or apply to several specified IP addresses. Here you have to choose whether you want to define a new rule regarding incoming traffic (inbound rules) or regarding outgoing traffic (outbound rules). If we want to create a rule regarding incoming traffic, we will have to select the inbound rules category and a list of all rules of the selected type will appear.
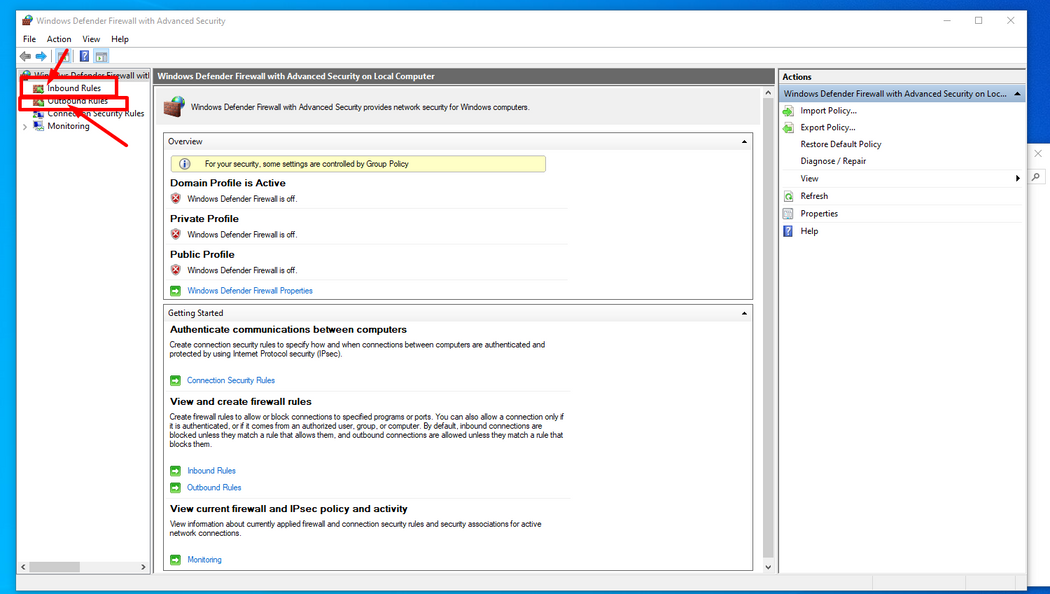 Here you must select the "new rule" option in the toolbar to the right.
Here you must select the "new rule" option in the toolbar to the right.
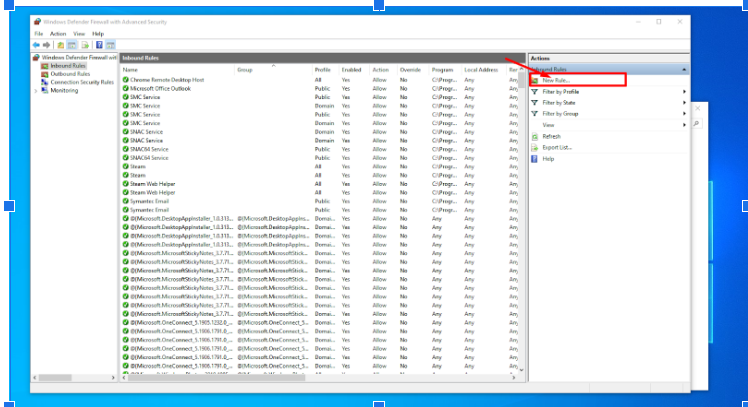
In the dialog box that will open, define the rule. You need to set the following: A. Does the rule refer to a program, a port, a unique connection to the Windows OS, or one that will be defined by the user. B. the source/destination port itself (depending on whether you are defining a rule which applies to incoming or to outgoing traffic), or the program depending on the previous option selected. C. The action that the rule dictates - prohibition, secure enabling, or complete enabling of traffic through the port. D. the Windows network profile for which the rule will be valid (private or public - of the domain). E. Its name, so that the user can easily recall his action, according to how it appears in the list. And.. now we have a shiny new rule. It is important to note that if there are two (or more) conflicting rules on the list, the uppermost one will take precedence over the others (ie the one added last). You can change the order of the items in the list (move the top ones to lower places, etc.)